There are several various kinds of data wellbeing. The three key categories are high, medium, and low. High-sensitivity data would cause catastrophic results on an corporation and low-sensitivity data would be attainable towards the public. Regardless of the different types, almost all data should be protected. To be able to prevent info from seeping into the incorrect hands, data sensitivity should be properly described and was able.
Data back up copies are an important part of data basic safety, and they support minimize the risk of unintended destruction. Back up copies also make sure that information is always available. This could be important in the instance of a infringement or ransomware attack. Nevertheless , many breaches of sensitive data will not occur as a result of hacking; they are really accidentally uncovered by employees. This could happen every time they share confidential information or perhaps allow usage of inappropriate persons. This frequently occurs as a result of employees’ not enough understanding regarding security procedures.
Data category is the strategy of classifying data by sensitivity and worth. This process is critical for businesses, since it helps all of them understand what info is useful and types of data safety whether it is in danger of being sacrificed. In addition , it may help organizations comply with GDPR and industry-specific legislation. Data classification workers may well employ software or perhaps manually review company data files to classify and protect info in different methods. For example , customer profiles are one type of high-sensitivity data, and the unauthorized access can result in huge consequences.
Data vaulting is another data defense strategy. This approach uses program to create multiple air-gapped clones of the stored data. This plan is more protect than typical data wiping. In addition , it verifies that the info cannot be retrieved. Another option is data erasure, which involves overwriting stored data, turning it unreadable.





















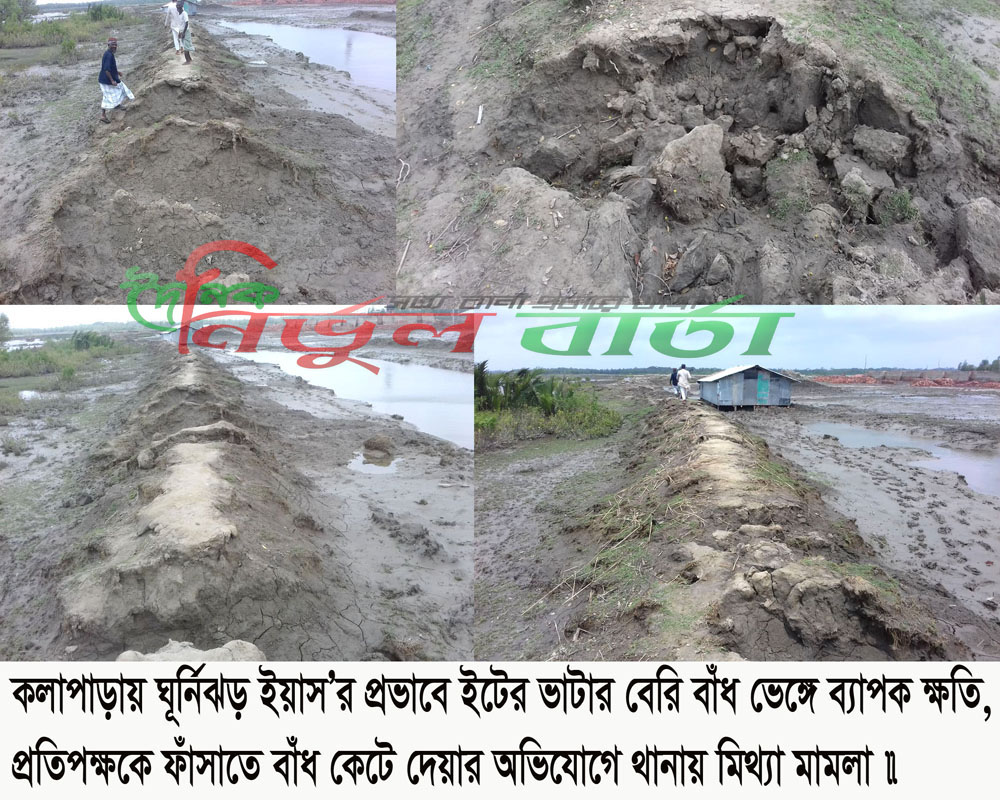




































































































![মাওলানা মামুনুল হক [ছবি: সংগৃহীত]](https://nirvulbarta.com/wp-content/uploads/2020/12/image-205495-1607591055.jpg)
![গ্রেফতার শাহনুর মিয়া [ছবি: ইত্তেফাক]](https://nirvulbarta.com/wp-content/uploads/2020/12/image-205492-1607589160.jpg)

















