
If you are taking into consideration purchasing internet security application, you are probably thinking about how functions. The best secureness software offers multiple levels of coverage, from real-time alerts to custom reports. Some internet security software packages also include computerized detection tools, as well mainly because access settings. However , technology alone are not able to solve every single information security problem, and proper staff training is important to minimize the chance of information loss. Most info breaches are due to human problem, so you may need to invest in secureness policies and staff training.
Other options consist of Heimdal CORP, which is customizable and designed for cloud users. Forcepoint can assist you define your network’s secureness policies, minimize content from being used by not authorized users, and block intrusion attempts. Reliability admins can also personalize SD-Wan, the industry centralized weeknesses management system. The technology can also keep an eye on and obstruct network activity using good alerts. Another popular reliability software program is Paros Proxy, which is depending on Java. It provides vulnerability readers, traffic recorders, and world wide web spiders, and can be designed easily.
Although smart devices are incredibly comfortable, their reliability capabilities are quite low. www.infosguards.net/avast-secureline-netflix-the-most-relevant-information Insecure equipment can allow online hackers to install viruses with them and track their users. Most brilliant devices connect with an internet router, so spyware from one contaminated device can spread to other equipment on the same network. Infected units may also accumulate personal information. Several fitness trackers even keep an eye on a customer’s health. This kind of security applications are essential for guarding data from theft.




















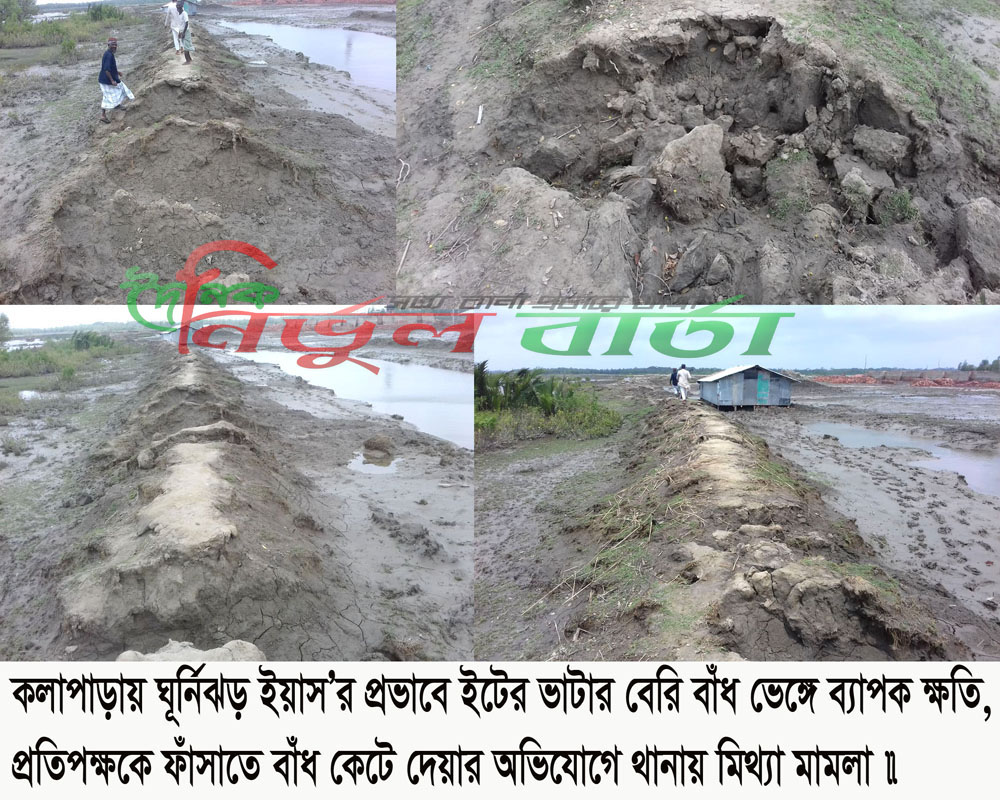




































































































![মাওলানা মামুনুল হক [ছবি: সংগৃহীত]](https://nirvulbarta.com/wp-content/uploads/2020/12/image-205495-1607591055.jpg)
![গ্রেফতার শাহনুর মিয়া [ছবি: ইত্তেফাক]](https://nirvulbarta.com/wp-content/uploads/2020/12/image-205492-1607589160.jpg)





















